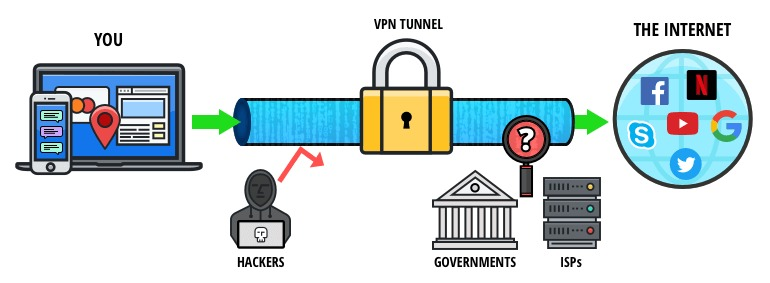
Virtual Private Network is a technology that allows you to connect to the internet via safe and encrypted tunnel to ensure that your online privacy and protect the data through hiding the IP address. This technology developed as a way to allow remote users and branch offices to securely access corporate applications and other resources.