What is Kube-Hunter?
As the name kube-hunter, its named for its ability to hunt for security weaknesses in Kubernetes clusters. Kube-hunter enables Kubernetes administrators, operators and security teams to identify weaknesses in their deployments and address those issues before attackers can exploit them.
Kube-hunter adds discovery and penetration testing capabilities to the CIS validation for K8s deployments offered by kube-bench. It functions similarly to an automated penetration testing tool in this regard.
Where should I run kube-hunter?
There are three different ways to run kube-hunter, each providing a different approach to detecting weaknesses in your cluster:
- Run kube-hunter on any machine (including your laptop), select Remote scanning, and give the IP address or domain name of your Kubernetes cluster. This will give you an attackers-eye-view of your Kubernetes setup.
- You can run kube-hunter directly on a machine in the cluster, and select the option to probe all the local network interfaces.
- You can also run kube-hunter in a pod within the cluster. This indicates how exposed your cluster would be if one of your application pods is compromised (through a software vulnerability, for example). (–pod flag)
There are three type of scanning Options available in Kube-hunter
1. Remote scanning
To specify remote machines for hunting, select option 1 or use the –remote option.Example: kube-hunter — remote some.node.com
2. Interface scanning
To specify interface scanning, you can use the –interface option (this will scan all of the machine’s network interfaces). Example: kube-hunter –interface
3. Network scanning
To specify a specific CIDR to scan, use the –cidr option. Example: kube-hunter –cidr 192.168.0.0/24
4. Kubernetes node auto-discovery
Set –k8s-auto-discover-nodes flag to query Kubernetes for all nodes in the cluster, and then attempt to scan them all. By default, it will use in-cluster config to connect to the Kubernetes API. If you’d like to use an explicit kubeconfig file, set –kubeconfig /location/of/kubeconfig/file.
Where should I run kube-hunter?
- On Machine
Clone the repository
git clone https://github.com/aquasecurity/kube-hunter.gitcd kube-hunter
pip install -r requirements.txtNow Run:
./kube-hunter.py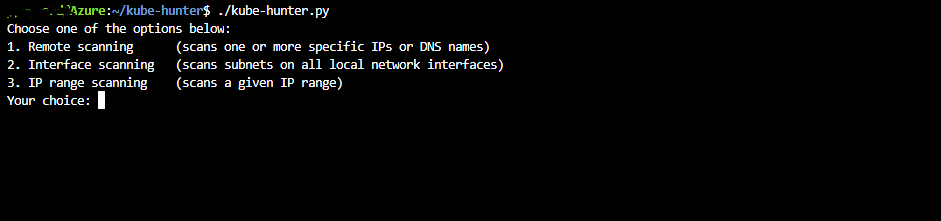
now you need to select from three options. In this example i am using “Remote Scanning”
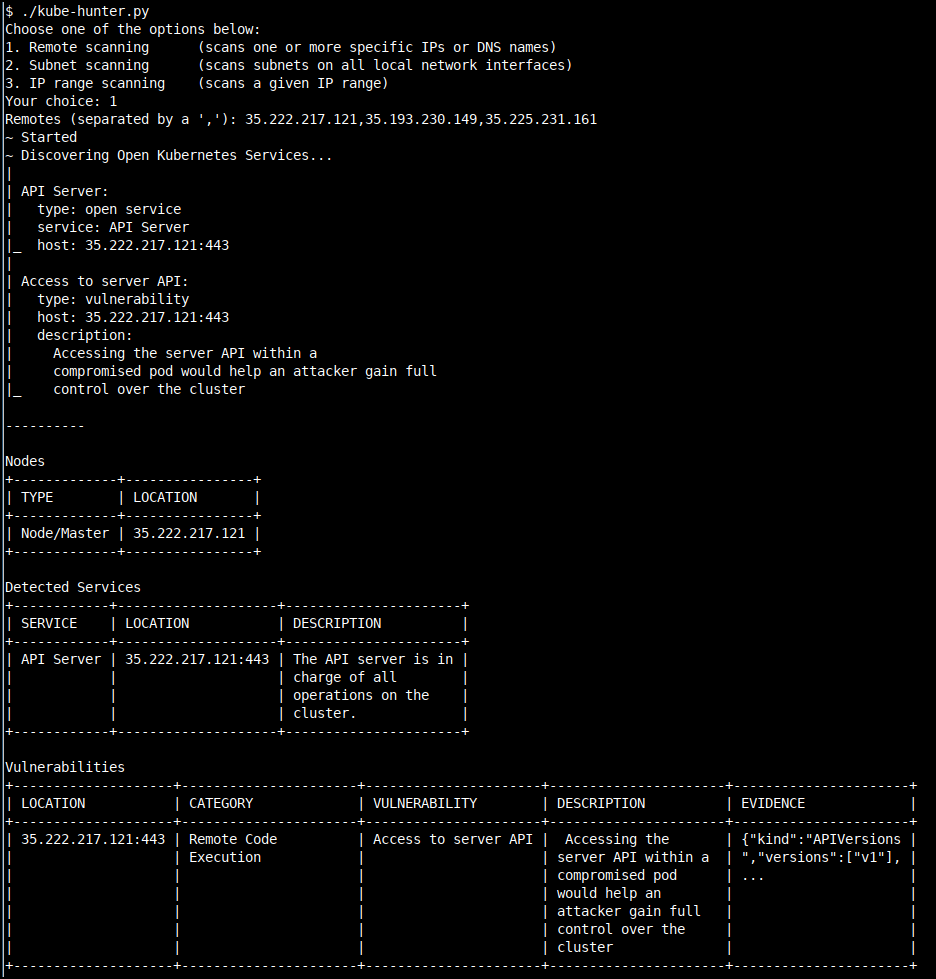
You will get the scan result above
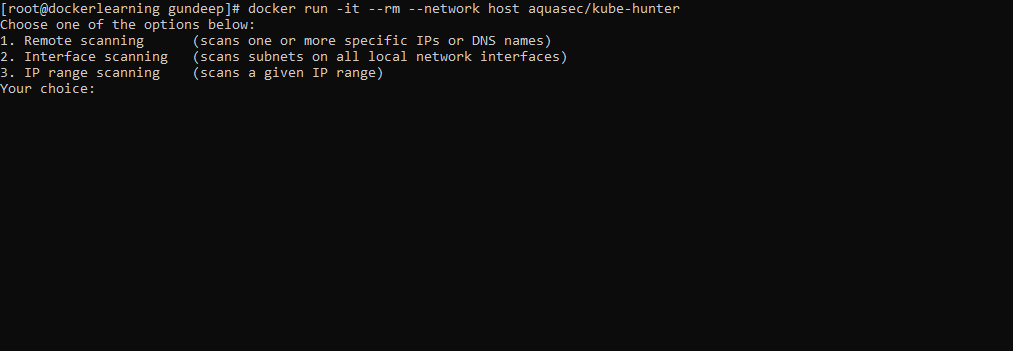
2. On Container
docker run -it --rm --network host aquasec/kube-hunterIt will again prompt you, like in step 1
3. Run as a pod
We can also run the kube-hunter as a active scan within the cluster as well
Create the below job
---
apiVersion: batch/v1
kind: Job
metadata:
name: kube-hunter
spec:
template:
metadata:
labels:
app: kube-hunter
spec:
containers:
- name: kube-hunter
image: aquasec/kube-hunter:0.6.8
command: ["kube-hunter"]
args: ["--pod"]
restartPolicy: NeverKubectl apply -f job-nameAfter creating the job it will create a pod
kubectl get po | grep kube-hunterNow view the report in pod logs
kubectl logs <pod_name>Be Responsible!
Never use kube-hunter on a cluster that belongs to someone else. It is possible to use this code to probe other websites, however the rules and regulations expressly prohibit this.
Thanks….. for reading Follow more Blogs on Cloudsbaba
References:




