In my previous blog, i post ,How to set up AWS SFTP Transfer using key based Authentication which is by default feature. In this blog i will show you how to configure SFTP Service using username and password based authentication.
Here we follow this architectural Diagram
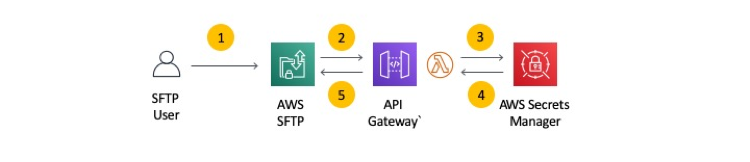
Steps We Follow :-
- Create a Stack using Cloud Formation Template.
- Create a SFTP Server.
- Store passwords and other stuffs in AWS Secret Manager.
- Test using winscp.
Step 1: Create a Stack using Cloud Formation Template.
The Cloud formation is a yml file which create API Gateway , Lambda function, three IAM Roles API Logging Role, API Gateway Access Role, Lambda Role for you.
Function of these roles:-
API Logging Role:- TransferApiCloudWatchLogsRole – Allows the API Gateway endpoint to log to CloudWatch Logs.
API Gateway Access Role:- TransferApiInvokerAssumeRole – Allows AWS SFTP to call the API Gateway endpoint, which means only services that you provide access to can use this API Gateway endpoint.
Lambda Role:- TransferLambdaExecutionRole – Allows the Lambda function to execute, and provides read-only access to Secrets Manager for secrets with the prefix SFTP/*.
Why we use Lambda function ?
The Lambda function is a relatively simple piece of Python code. It takes the input parameters from the incoming API Gateway request and looks up the user name (in the format SFTP/Username) as a secret in Secrets Manager.
- If the password is passed through to the function by AWS SFTP, authenticate the user by password so that it is validated against the password stored within the secret.
- If the password is blank, then authenticate the user by SSH key and pass the stored public keys back to AWS SFTP
Lets Start.
Download the Cloudformation Template from ,,here.
- Navigate to Cloud formation Service in AWS
Click “Create Stack”
- Upload a template file that we download from the link that is provided above
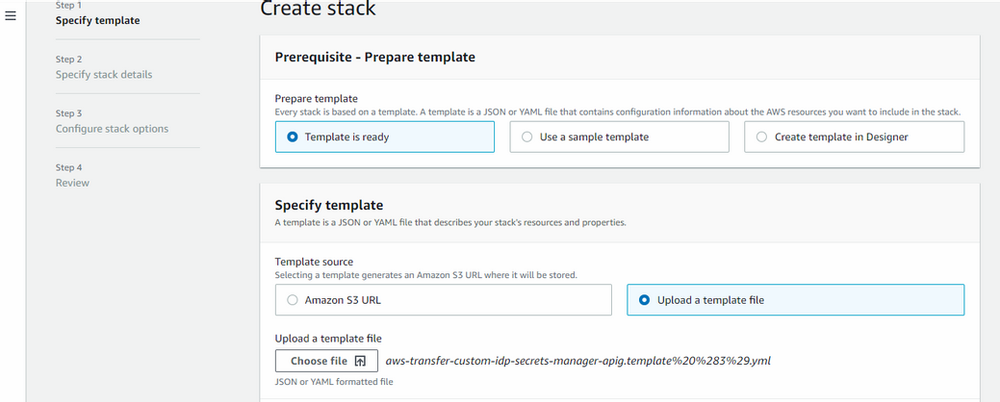
click “next”
- Provide the name to stake and leave all other tabs as it is.
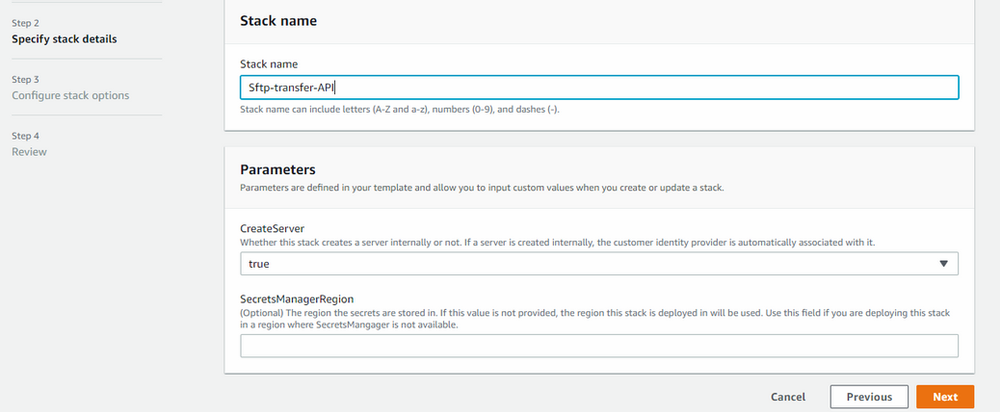
Click “Next”
- In configure stack options click “Next”
- Review the stack and create it.
As you see in Cloudformation your stack is in progess
it will take 5-10 min to complete.
After it is created you can check it from an API Gateway Service
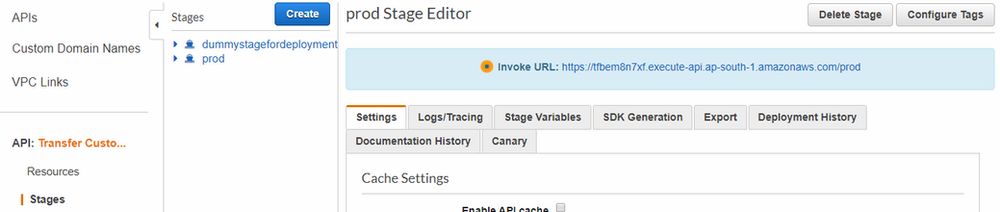
Copy the Invoke URL from the API gateway which we are going to use in next step
Step 2: Create a SFTP Server.
- Navigate to AWS SFTP Transfer Family
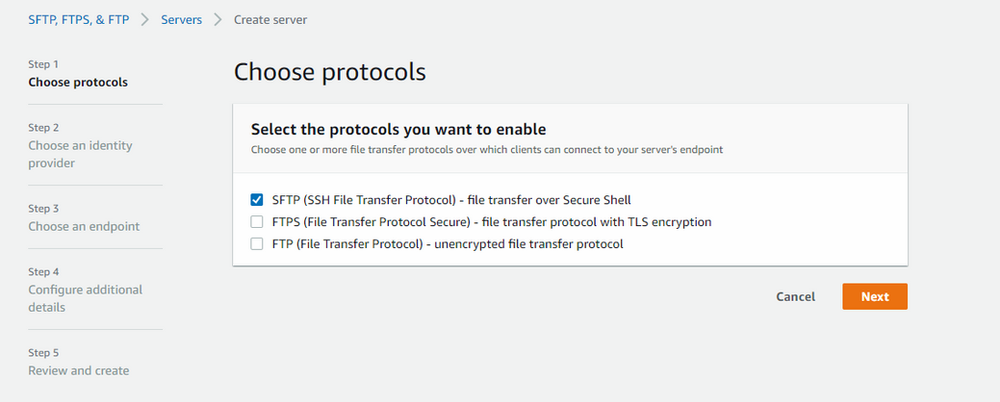
Click “Next”
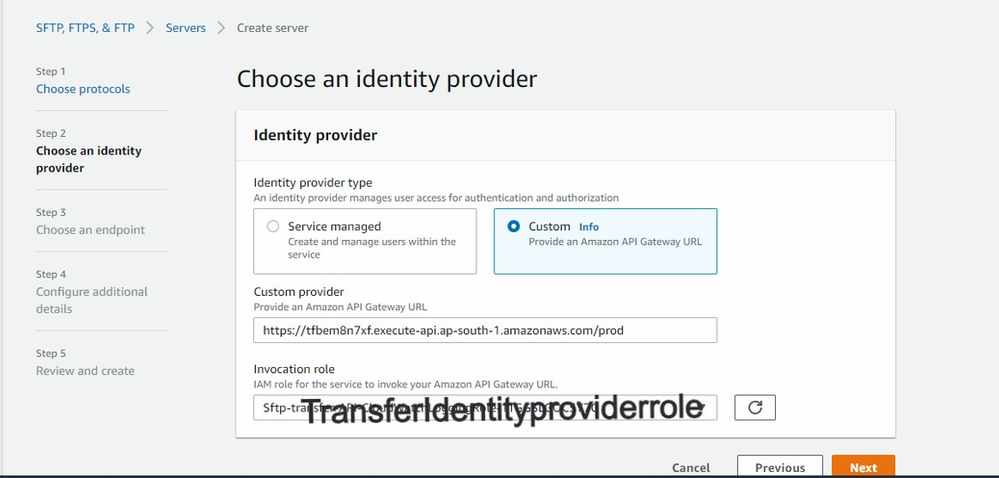
- Paste the URL in Custom provider that we copied from API Gateway
- In the Invocation role Select the TransferIdentityproviderrole.
- Click “Next”
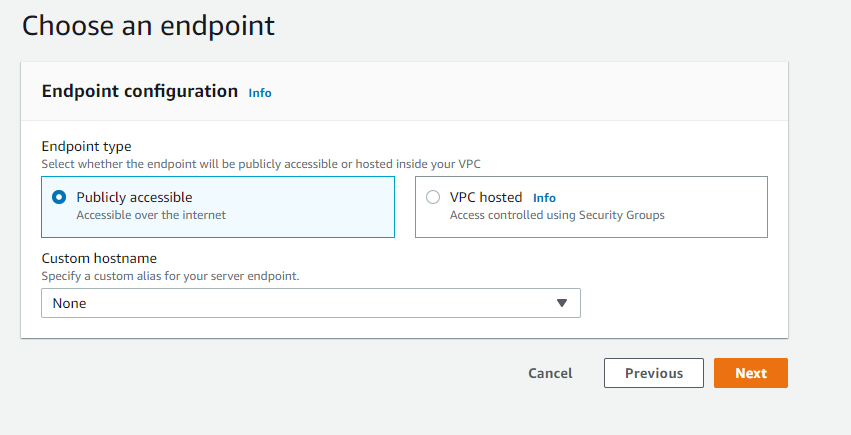
- Select the Endpoint for you sftp server
If you want your sftp server is publicly accessible then we use Public accessible or else we use VPC hosted
Click “Next”
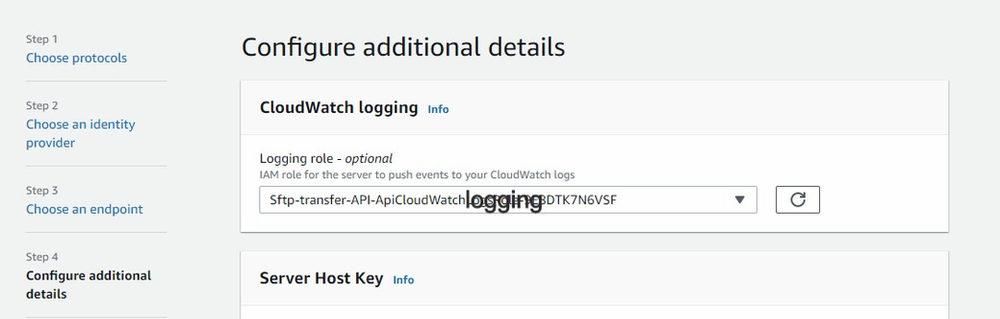
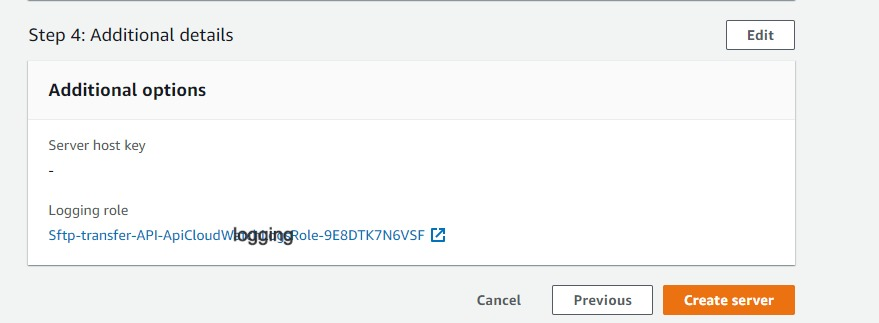
- Select cloud watch logging role for all the API call logging
click “Next”
Click “Create server”
Step 3: Manage credentials using Secret Manager
Now you understand how custom authentication for AWS SFTP works, here’s a secure data store with a RESTful API in which to store your user data: Secrets Manager.
Create user entries along with your custom attributes (password, IAM role, and HomeDirectory value) in an encrypted store with Secrets Manager. You can provide granular access to only those who require it.
You can’t directly connect AWS SFTP to Secrets Manager today, so you will use a Lambda function that provides the logic to connect them. This Lambda function is responsible for validating the user credentials against the one stored, and return access information.
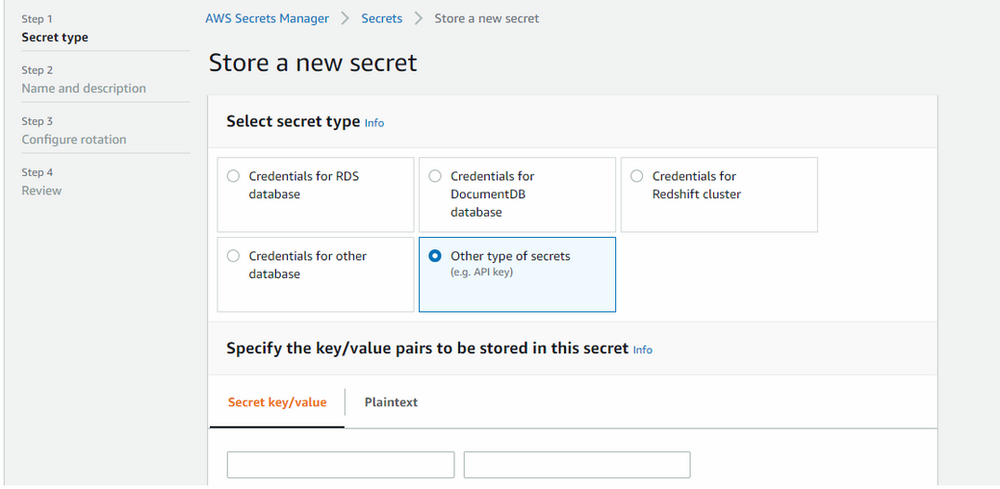
- Navigate to AWS Secret Manager
- Select “other type of secret”.
- Create key pair value
Use the following Json to create key value pair
{
"Password": "Admin123",
"Role": "arn:aws:iam::877305103254:role/Role-for-accessing-s3",
"HomeDirectory": "/cloudsbucket001"
}Role:- copy the role arn for accessing S3 bucket. Make sure you have a policy for accessing S3 bucket.copy policy from here
HomeDirectory:- Directory of the Bucket
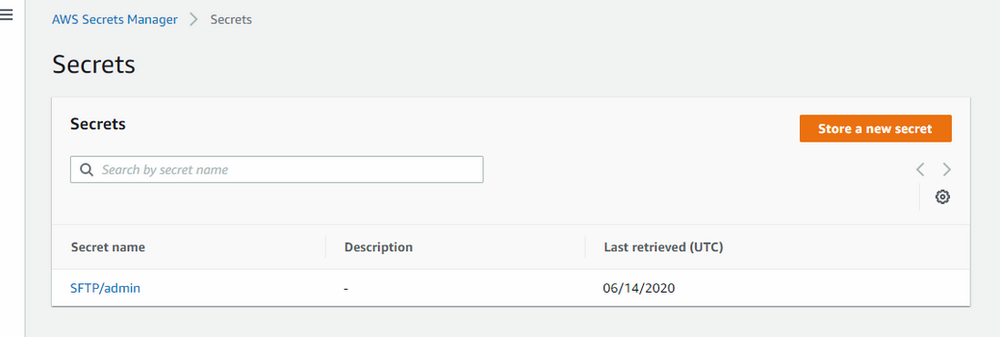
- Save the Secret key with sftp/user_name. e.g SFTP/cloudsbaba
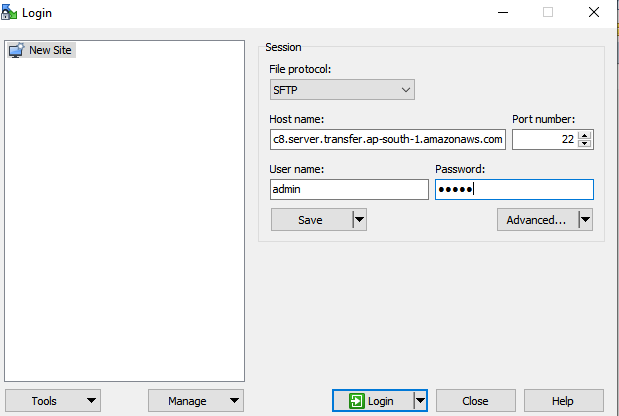
Step 4: Test using winscp
copy the end point from SFTP Transfer service
username and password that we created in Secret manager
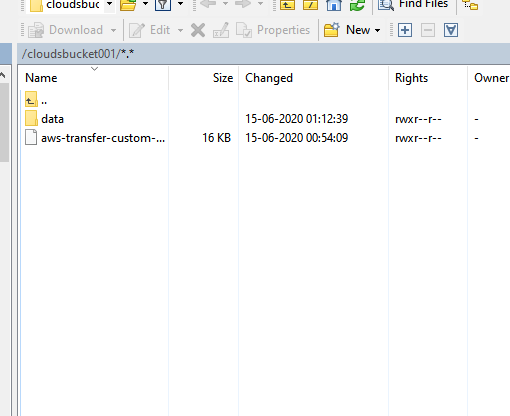
Now you are able to access the sftp service using password authentication.
Congratulation….. you follow all the steps and configured SFTP server with Password based authentication..
For more content please subscribe www.cloudsbaba.com
Reference:-



