AWS Backup is a fully managed backup service that makes it easy to centralize and automate the backup of data across AWS services. Using AWS Backup, you can centrally configure backup policies and monitor backup activity for AWS resources, such as Amazon EBS volumes, Amazon EC2 instances, Amazon RDS databases, Amazon DynamoDB tables, Amazon EFS file systems, and AWS Storage Gateway volumes. AWS Backup automates and consolidates backup tasks previously performed service-by-service, removing the need to create custom scripts and manual processes. With just a few clicks in the AWS Backup console, you can create backup policies that automate backup schedules and retention management. AWS Backup provides a fully managed, policy-based backup solution, simplifying your backup management, enabling you to meet your business and regulatory backup compliance requirements.
How it works?
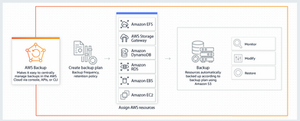
- Create a SNS topic to send AWS Backup notifications.
- Make Sure your user has permission to call this backup API.
- Configure your backup vault to send notifications to the SNS topic.
- Create an SNS subscription that filters notifications to backup jobs that are unsuccessful(optional).
- Test for notifications.
Step 1- Create an SNS(Simple Notification Service) topic to send AWS Backup notification.
Navigate to SNS Service and Create Topic
Click “Create Topic”
After the topic is created copy the ARN and keep it safe because it is used in next steps
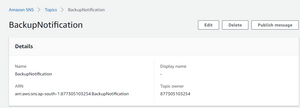
ARN:- arn:aws:sns:ap-south-1:877305103254:BackupNotification
Click on “Edit”
Scroll down and expand Access policy
Replace the existing policy with the below json
{
"Version": "2008-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "__default_statement_ID",
"Effect": "Allow",
"Principal": {
"Service": "backup.amazonaws.com"
},
"Action": "SNS:Publish",
"Resource": "arn:aws:sns:us-east-1:111111111111:demo"
}
]
}
Click “Save”
Note: Make sure that Resource ARN is replace with the one you copied in further step
Step 2- Create a policy that has permission to call backup API.
Navigate to IAM role and policies
Create a new policy with the name as per your choice and below permisssions
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"backup:ListBackupPlans",
"backup:ListBackupJobs",
"backup:PutBackupVaultNotifications",
"backup:GetBackupVaultNotifications",
"backup:ListBackupVaults"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "backup:*",
"Resource": [
"arn:aws:backup:*:*:backup-vault:*",
"arn:aws:backup:*:*:backup-plan:*"
]
}
]
}
Save Policy
Create a role and attach this newly created policy to a role
In my case Role name is Backup_API and Policy name is Backuppolicy
Attach this role to the EC2_Instance
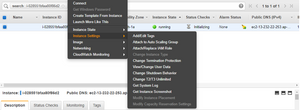
As you can see in the instance Description role is attached

Step 3- Configure backup vault
Navigate to AWS Backup
Click Backup vaults on the left
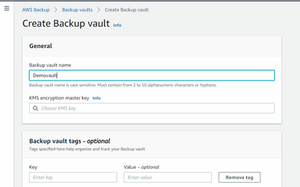
Click “create backup Vault”
Click on “Backup Plans”
Create Backup Plan
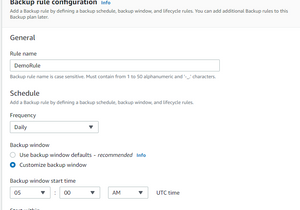
Backup Rule Configuration
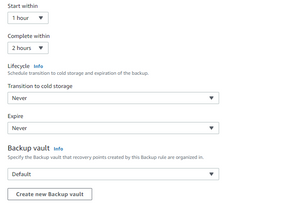
Click “Create Plan“
After the Backup plan is created, navigate Resource assignments
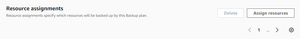
Specify which resource will be backed up by backup plan
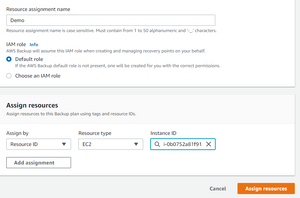
Click “Assign resources”
Step 4- Enable the backup notification from EC2 instance.
Login to EC2 Instance
Install AWSCLI
- Using the AWS CLI, run the put-backup-vault-notifications command with –backup-vault-events set to BACKUP_JOB_COMPLETED. Replace the following values in the example command:
–endpoint-url: Enter the endpoint for the AWS Region that your backup vault is in. –backup-vault-name: Enter the name of your backup vault. –sns-topic-arn: Enter the ARN of the SNS topic that you created.
Command
aws backup put-backup-vault-notifications --backup-vault-name Demovault --sns-topic-arn arn:aws:sns:ap-south-1:877305103254:BackupNotification --region 'ap-south-1' --backup-vault-events BACKUP_JOB_COMPLETED
Run the get-backup-vault-notifications command to confirm that notifications are configured:
aws backup get-backup-vault-notifications --backup-vault-name Demovault --region 'ap-south-1'
This command return output similar to this :
{
"BackupVaultName": "Demovault",
"BackupVaultArn": "arn:aws:backup:ap-south-1:877305103254:backup-vault:Demovault",
"SNSTopicArn": "arn:aws:sns:ap-south-1:877305103254:BackupNotification",
"BackupVaultEvents": [
"BACKUP_JOB_COMPLETED"
]
}
Step 5- Create SNS subscription and filter the notifications according to your requirement
In this tutorial i am not filtering any notification i am getting all the notifications,if you want notification on job fails i am also do that for you all.
Again navigate to SNS
Click on create “Subscriptions”
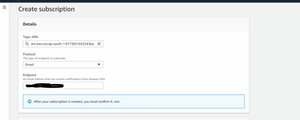
This is for all backup notifications
If you want only unsuccessful backup notifications then expand Subscription filter policy and add the below script:-
{
"State": [
{
"anything-but": "COMPLETED"
}
]
}
This will notify you only when the backup fails
Click “Create Subscription”
Step 6- Test for Notification
Create on demand backup of the EC2-Instance .
when the backup for ec2-instance is completed you will get a notification like this
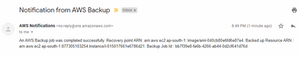
And when the job stopped by user or failed its look like this
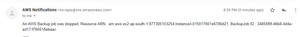
Kudos…! you successfully completed all the steps and configured backup notifications for successful and backup fails backups.



